OSI: Transport Layer - Layer 4 (Part 5)
Definition
The Transport layer (layer 4) is responsible for the reliable and efficient communication between programs called endpoints.The exchange can be peer-to-peer (e.g., an instant messaging application) or it can be a client/server interaction (e.g., a Web browser sending a request to a Web server).
Responsibilities
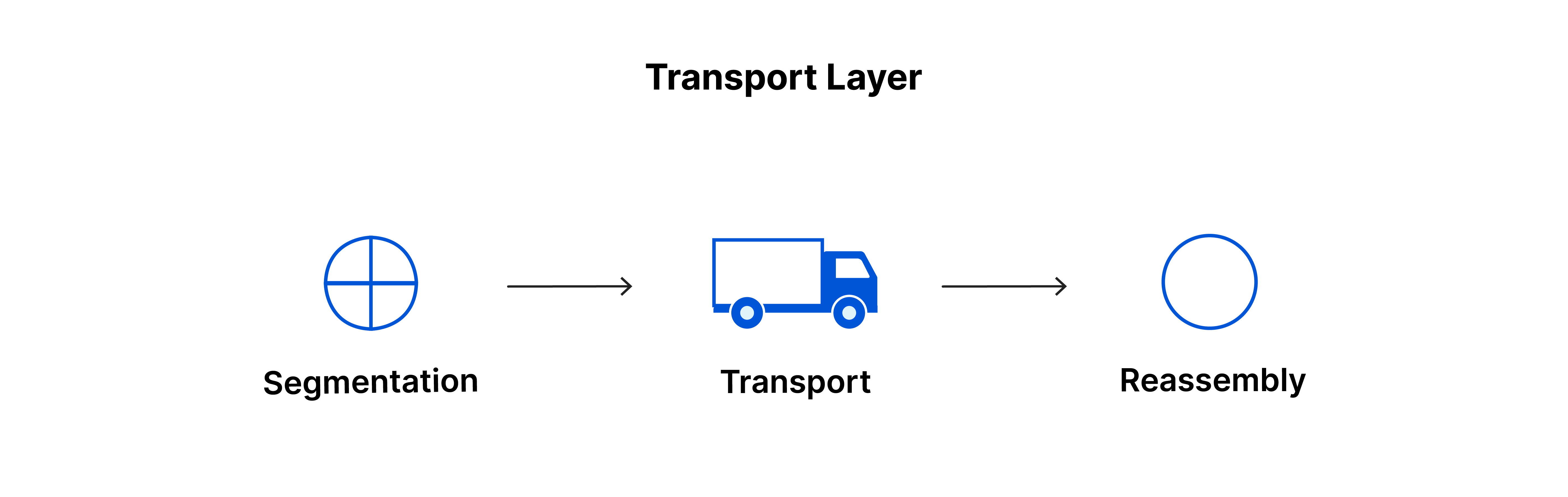
The Transport layer is responsible for end-to-end communication. It ensures that data is transferred reliably and without errors. Whereas the application, presentation, and session layers are primarily concerned with data, the transport layer is focused on segments.
Segments are the packets of data that are sent between devices. They contain the data being transferred, as well as control information like source and destination ports, sequence numbers, and error-checking data.
On the sending side, the Transport layer takes data from the Session layer and breaks it into segments for the Network layer. On the receiving side, it reassembles the segments from the Network layer and passes them on to the Session layer.
Depending on the application protocol being used, the Transport layer can send data either quickly or reliably.
Transport layer responsibilities include end-to-end error recovery and flow control.
Protocols
Two kinds of protocols are encountered at the Transport layer: connection-oriented (like TCP) and connectionless (like UDP).
Each protocol has pros and cons that motivate programmers to select one depending on what he or she is trying to accomplish via the network.
End users do not choose what protocol is used, that is a programming decision. Generally, trivial and ad-hoc exchanges across the network are done in a connectionless manner. More persistent network relationships are largely handled with connection-oriented solutions, especially when a substantial amount of data is being transferred.
At the Transport layer you will find additional error checking and retransmission logic to ensure that all of the messages sent arrive intact at the receiving end.A checksum or similar mechanism is generally used to ensure message integrity. Retransmission strategies vary, however, in the case of TCP, data that is not positively acknowledged by the recipient in a timely way is retransmitted.
Why do we need both connection-oriented and connectionless protocols?
By nature, connections are point-to-point. A program on one system forms a session with another program, usually on another system. What happens if you need to broadcast or multicast onto the network? These operations are point-to-multipoint in nature. In these cases, the sender is often not aware of the number of potential recipients of his or her transmission. How can you have a connection with an unknown number of recipients? You can’t, which flies in the face of the concept of a connection.
Also, there is some network overhead associated with the establishment of connections and with their subsequent dissolution. For example, when using TCP there is a three-packet exchange to establish a connection, and there is typically a four-packet conversation that tears down the connection. Sometimes that overhead is unwarranted.
Let’s take a look at the two most common Transport layer protocols TCP and UDP. There are a lot of interesting things to learn about them. But we will try to focus on the most important ones in context of the OSI model.
-
TCP (Transmission Control Protocol): A connection-oriented protocol that provides reliable communication using handshaking, acknowledgments, error control, and session teardown.
-
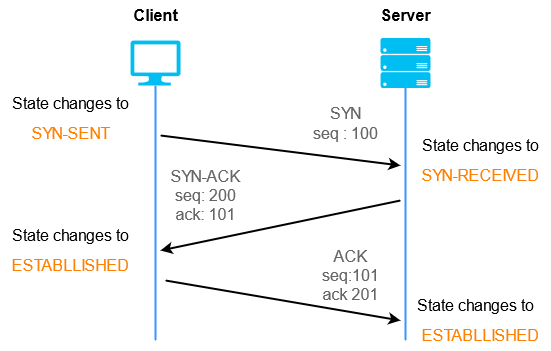
Handshaking: The process of establishing a connection between two devices. It involves a series of messages to negotiate parameters and ensure both devices are ready to communicate.
The concept of handshaking is more closely related to the session layer than the transport layer in the OSI model. However, it is a critical part of the TCP protocol, which operates at the transport layer.
-
Step 1 (SYN): In the first step, the client wants to establish a connection with a server, so it sends a segment with SYN(Synchronize Sequence Number) which informs the server that the client is likely to start communication and with what sequence number it starts segments with
-
Step 2 (SYN + ACK): Server responds to the client request with SYN-ACK signal bits set. Acknowledgement(ACK) signifies the response of the segment it received and SYN signifies with what sequence number it is likely to start the segments with
-
Step 3 (ACK): In the final part client acknowledges the response of the server and they both establish a reliable connection with which they will start the actual data transfer
-
-
Acknowledgments: The process of confirming that data has been received successfully. When a device receives data, it sends an acknowledgment back to the sender to confirm the successful receipt of the data.
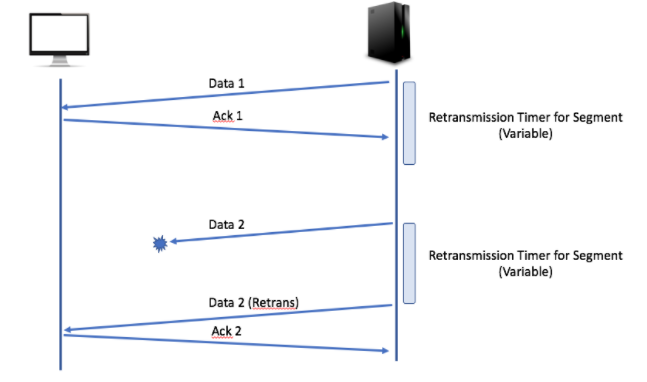
The client sends an ACK signal to the server after successfully receiving data. This ACK acknowledges that the specific data segment arrived without errors. This two-way handshake mechanism helps prevent data loss and corruption.
-
Error Control: TCP Error Control Mechanisms: TCP employs several techniques for error control, including:
- Checksums: Every TCP segment contains a checksum calculated by the sender and verified by the receiver. Any discrepancy in the checksum indicates data corruption during transmission.
- Sequence Numbers: TCP assigns sequence numbers to each data segment, ensuring packets arrive in the correct order at the receiver.
- Acknowledgements (ACKs): The receiver sends ACKs to the sender to confirm successful reception of data segments. Retransmissions occur if ACKs are not received within a timeout period. (You can see an example on the image above)
-
Session Teardown: The process of closing a connection between two devices. When data transfer is complete, the devices exchange messages to gracefully close the connection and release resources.
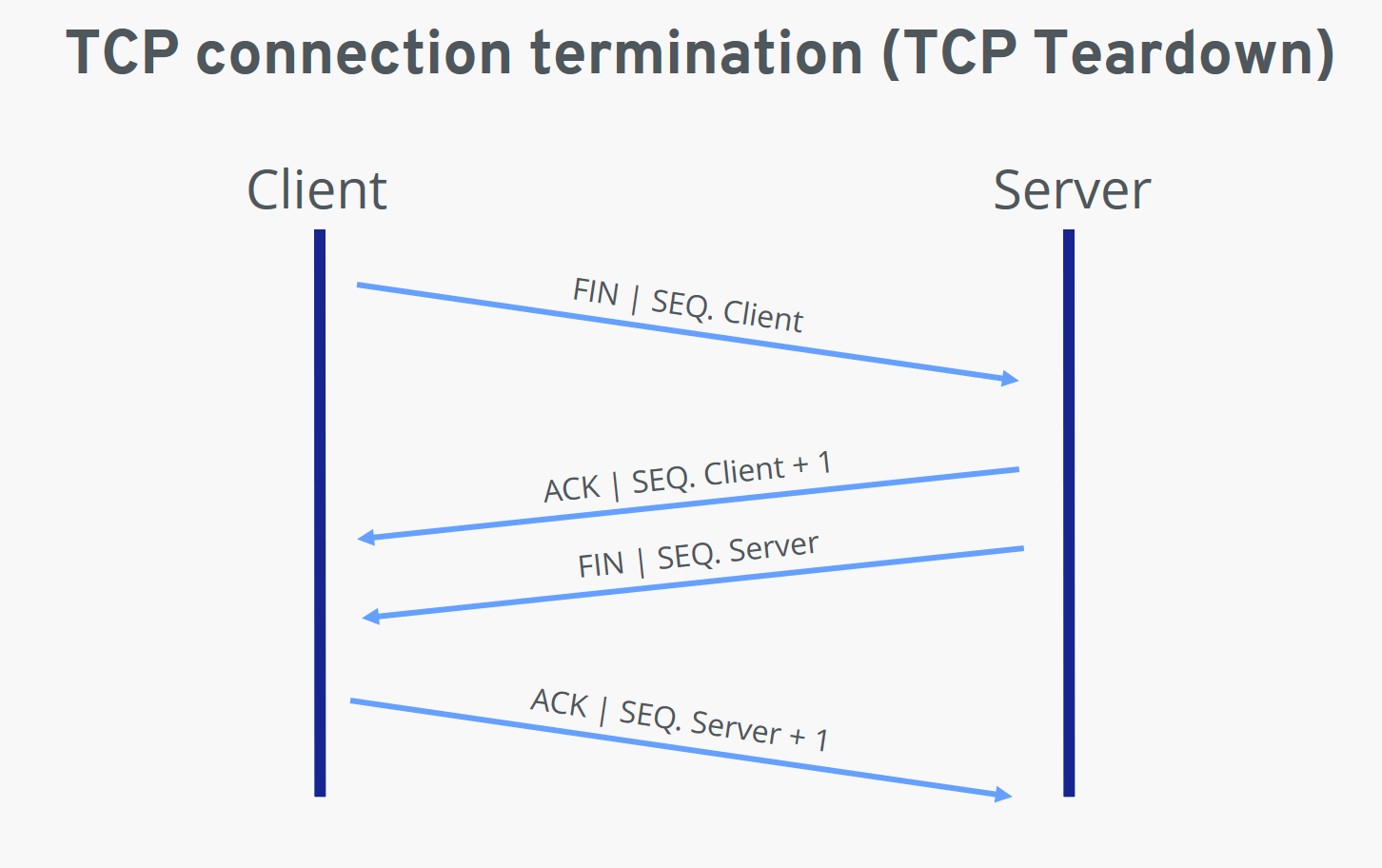
As you could guess, the teardown process also closely relates to the session layer in the OSI model.
-
-
UDP (User Datagram Protocol): A connectionless protocol that provides fast, lightweight communication without the overhead of TCP.
- Connectionless: UDP is a connectionless protocol, meaning it does not establish a connection before sending data. This makes it faster and more efficient for transmitting small, time-sensitive packets.
- Low Overhead: UDP has lower overhead than TCP because it does not include error-checking mechanisms like acknowledgments and retransmissions. While this makes UDP faster, it also means that data sent over UDP may be lost or corrupted without detection.
- Unreliable: UDP does not guarantee delivery of data packets, so it is often used for real-time applications like video streaming and online gaming.
- Datagrams: UDP sends data in small, self-contained packets called datagrams. Each datagram includes the source and destination ports, as well as the data payload.
- Stateless: UDP is a stateless protocol, meaning it does not maintain connection state information between packets. This allows for faster transmission but can lead to packet loss or out-of-order delivery.
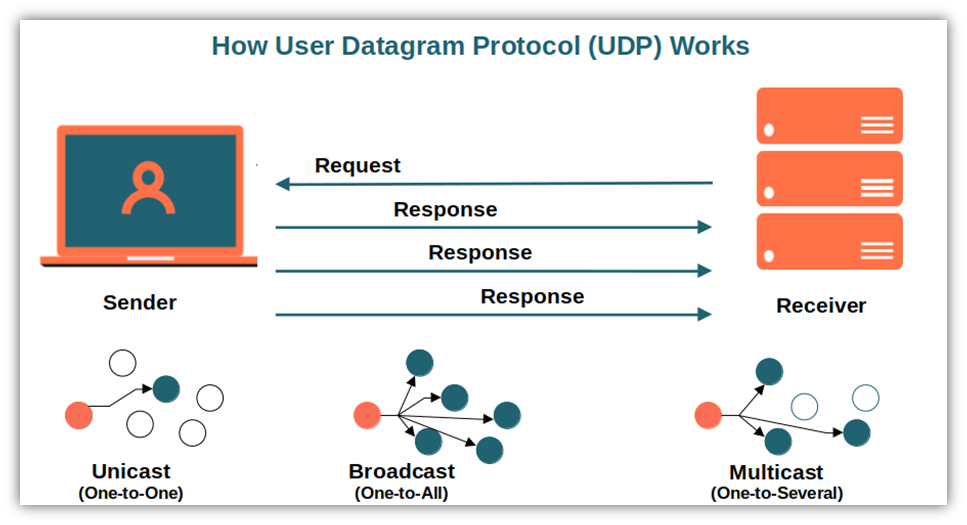
UDP is commonly used in time-sensitive communications where occasionally dropping packets is better than waiting. Voice and video traffic are often sent using this protocol because they are both time-sensitive and designed to handle some level of loss.
And while UDP is faster than TCP, it is not as reliable. If you are sending a file, you want to use TCP. If you are sending a live video stream, you might want to use UDP.
Since TCP is connection-oriented, it can transfer data only between two devices (unicast). UDP, on the other hand, can transfer data to multiple devices (multicast) or to all devices on the network (broadcast).
Conclusion
The Transport layer is a critical part of the OSI model, responsible for end-to-end communication between devices.
- It ensures that data is transferred reliably and without errors.
- The Transport layer is focused on segments, which are packets of data sent between devices.
- Two common Transport layer protocols are TCP (connection-oriented) and UDP (connectionless).
- TCP provides reliable communication with handshaking, acknowledgments, error control, and session teardown.
- UDP provides fast, lightweight communication without the overhead of TCP, making it ideal for time-sensitive applications.
In the next post, we’ll explore the Network layer and its role in routing packets across the network. Stay tuned!