OSI: Application Layer - Layer 7 (Part 2)
Definition
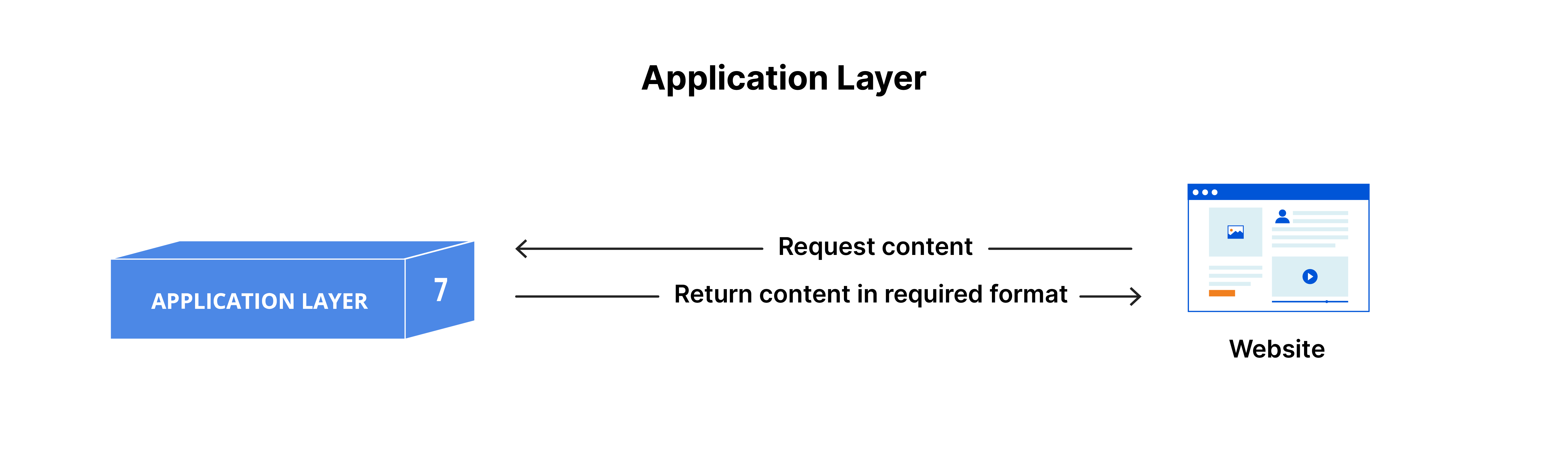
The application layer sits at the top of the Open Systems Interconnect (OSI) seven-layer model, providing network access to applications and users.
This is the only layer that directly interacts with data from the user. Software applications like web browsers and email clients rely on the application layer to initiate communications. But it should be made clear that client software applications are not part of the application layer; rather the application layer is responsible for the protocols and data manipulation that the software relies on to present meaningful data to the user.
Responsibilities
The application layer is responsible for providing network services directly to the user. It provides a platform for software applications to communicate over a network. The application layer is responsible for identifying and establishing the availability of the intended communication partner, determining resource availability, synchronizing communication, and establishing agreement on procedures for error recovery and control of data integrity.
Protocols
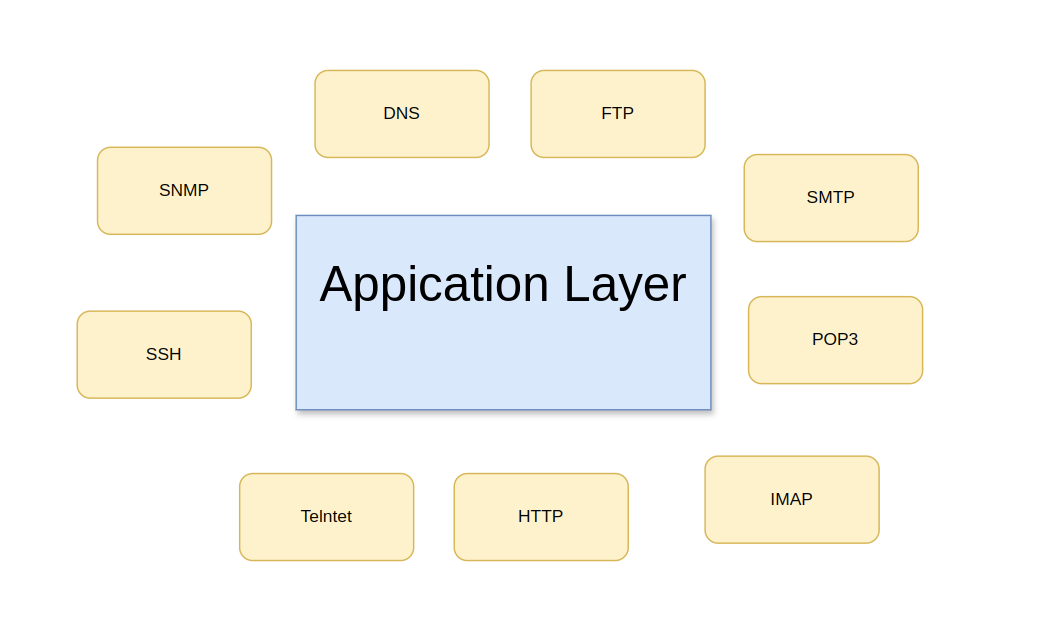
On the image above you can see some of the protocols that are used on the application layer. Let’s take a look at them in more detail:
Note: It’s important to note that while each protocol operates on the Application Layer, it might rely on lower layers in the OSI model for the actual network communication and data transmission. Be aware of that reading further.
-
DNS (Domain Name System) acts like a phonebook for the internet. It translates human-readable domain names (like
https://google.com) into numerical IP addresses (like142.250.184.196) that computers use to locate and connect to websites.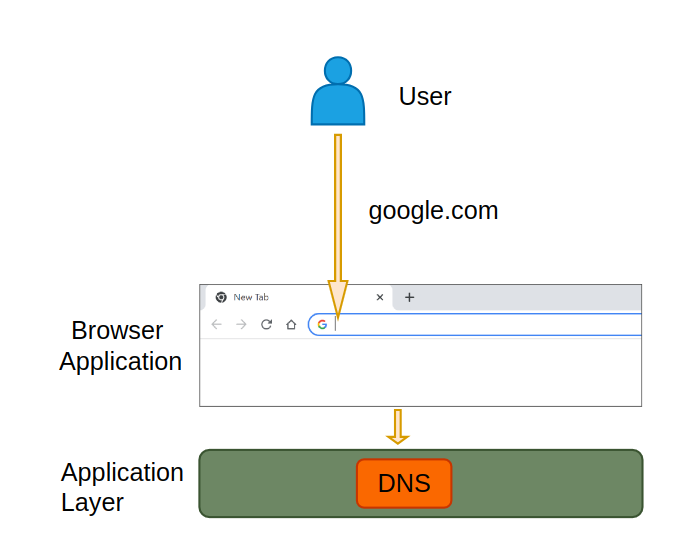
-
FTP (File Transfer Protocol) is a standard way to transfer files between computers over a network. It allows you to upload files to a remote server (like sending files to a website) or download files from a remote server (like downloading software or documents).
-
SMTP (Simple Mail Transfer Protocol) is a standard protocol used for sending email messages between servers over a network. It defines how email clients (like Gmail or Outlook) communicate with mail servers to deliver outgoing emails.
-
HTTP (Hypertext Transfer Protocol) is the foundation of data communication on the World Wide Web. It defines how web browsers and servers communicate to request and deliver web pages, images, videos, and other resources.
-
POP3 (Post Office Protocol version 3) is a standard protocol used by email clients to retrieve email messages from a mail server. It allows users to download emails from the server to their local computer or device.
-
IMAP (Internet Message Access Protocol) is another standard protocol used by email clients to retrieve email messages from a mail server. It allows users to view and manage email messages on the server without downloading them to their local computer or device.
-
SSH (Secure Shell) is a cryptographic network protocol used for secure remote access to computers over an unsecured network. It provides a secure channel for data communication, remote command execution, and other network services.
-
SNMP (Simple Network Management Protocol) is a standard protocol used for monitoring and managing network devices like routers, switches, servers, and printers. It allows network administrators to collect information, monitor performance, and manage network devices remotely.
-
Telnet (Teletype Network) is a network protocol used for remote terminal access to computers over a network. It allows users to log in to a remote computer and execute commands as if they were sitting in front of the computer’s console.
While Telnet isn’t entirely obsolete, its use is very limited and discouraged in most situations. Secure alternatives like SSH are readily available and offer a much safer approach for remote access and communication. If you encounter Telnet, it’s a strong recommendation to use a more secure protocol whenever possible.
These protocols are just a few examples of the many protocols that operate on the application layer. At the same time they are some of the most common and widely used protocols in the networking world.
Conclusion
- The application layer is the top layer of the OSI model, providing network services directly to the user.
- It is responsible for enabling software applications to communicate over a network and interact with data from the user.
- The application layer relies on lower layers in the OSI model for actual network communication and data transmission.
- It is home to a wide variety of protocols that enable different types of network communication, including web browsing, email, file transfer, and remote access.
In the next post, we will dive into the Presentation layer of the OSI model. Stay tuned!